The importance of cybersecurity is on the rise. There is no fully protected computer network. The most secure system is that which is not connected to the internet. If you are connected to the internet then the risk of a cyber attack on your system is always there.
Types of cyber-attacks
Here we are going to discuss different types of cyberattacks:
Malware
Malware is a piece of code that can cause a variety of malicious activities. Some types of malware are designed to get persistent access to a network, to get credentials or valuable information. The most common form of malware is Ransomware-a program designed to encrypt the files of the infected system.
Phishing attack
Phishing attacks are often carried out by sending an email or a mobile message pretending to be a form of a legitimate organization, like your bank, the tax department, or any other trusted entity. The main aim of this attack is to grab valuable information like credit card numbers, passwords, and so on.

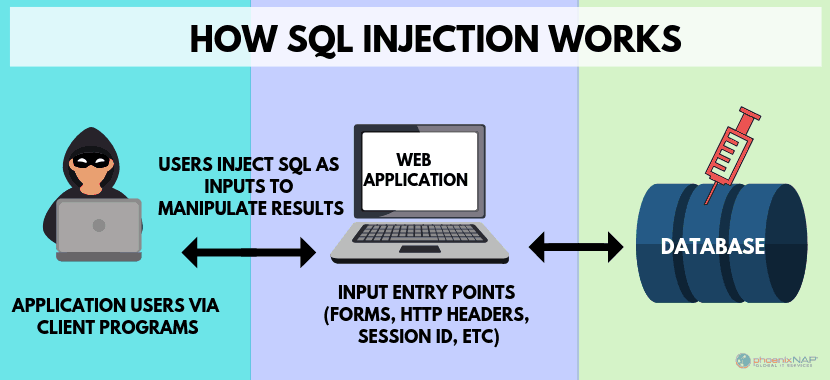
SQL injection
SQL injection is a type of attack specified to SQL database. In SQL injection SQL statement is used to query the data, and this statement is typically executed via an HTML form on a webpage. In this kind of the attackers may get access to read, modify or delete the data stored in the database.
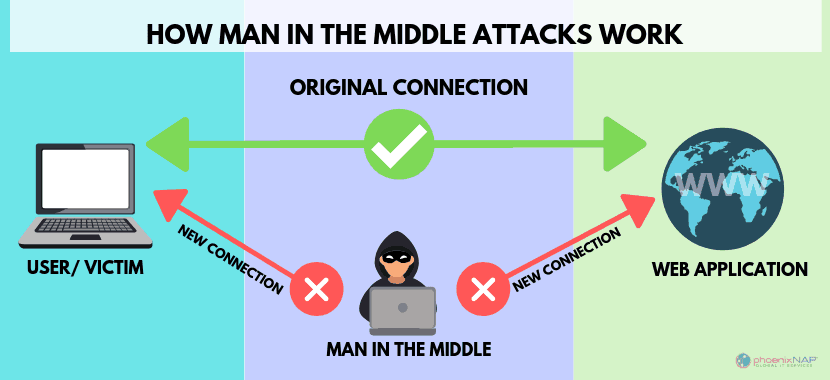
Man-in-the-middle attack
A Man-in-the-Middle-Attack(MITM) is a type of attack in which an attacker comes in between two communicating parties. The attacker hijacks the session between a client and host. By doing so the hackers steal useful information.
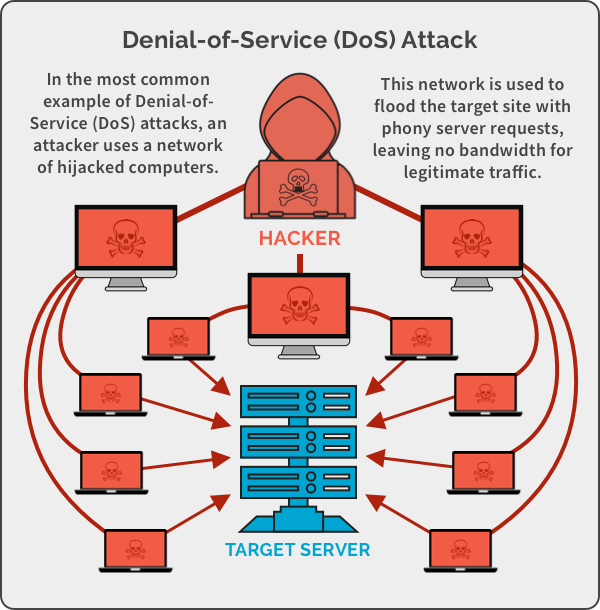
A denial-of-service attack(Dos attack)
A Denial-of-service attack is an important risk to companies. Here, hackers target systems, servers, or networks and flood them with traffic to exhaust their resources and bandwidth.
When this occurs, catering to the incoming requests turns out to be irresistible for the servers, resulting in the website it hosts either shut down or slow down. This leaves the legitimate service requests unattended.
It is also recognized as a DDoS (Distributed Denial-of-Service) attack when attackers use multiple compromised systems to launch this attack.
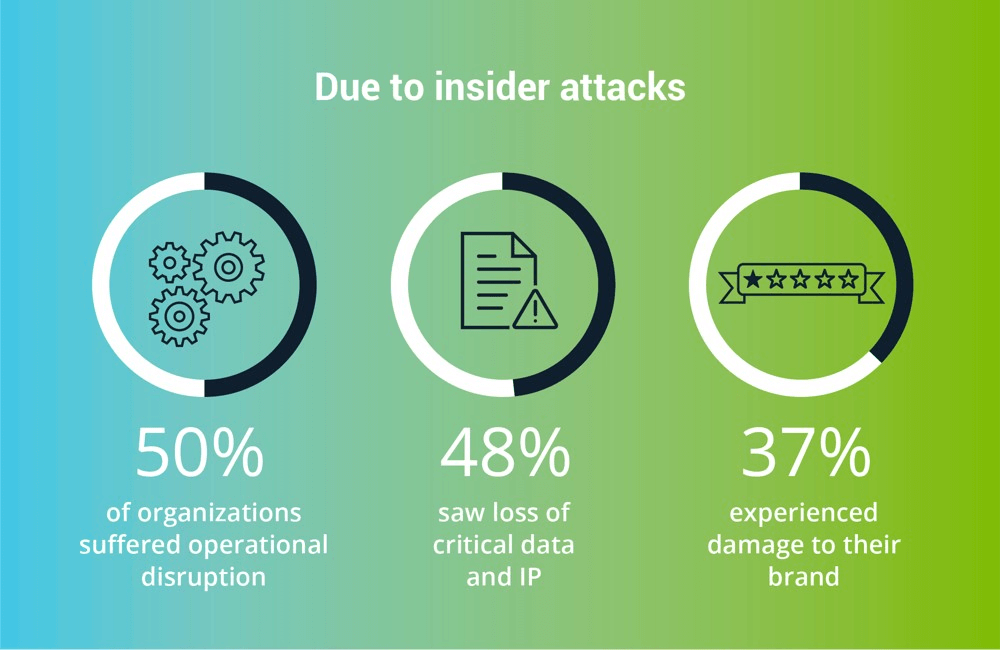
Inside attack
An insider attack does not involve a third party but an insider. In such a case; it could be a person from within the organization who knows everything about the organization. This kind of attack has horrifying consequences, to avoid such attacks develop multiphase passwords and security checks.
Insider threats are out of control in small businesses, as the staff there holds access to multiple accounts with data.
How we can ensure cybersecurity
We should try to understand that cyber threats are real, we can ensure cybersecurity by following the instructions given below:
Clicking without thinking is reckless
Malicious links can harm you and your organization a lot. So beware before clicking any ambiguous link, there are many suspected sites and programs that are filled with malware. Be careful when you are downloading any application from an unidentified source.

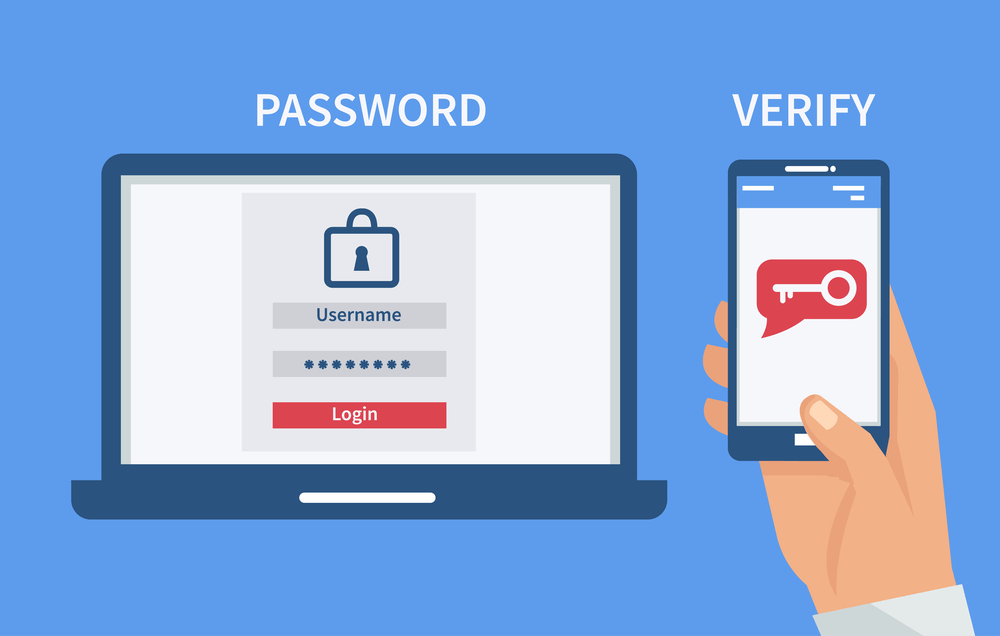
2.Use two-factor authentication
You must have a strong password, but two layers of authentication are necessary for organizational safety and security.
3.Look out for phishing scams
It’s estimated that around 3 billion fake emails are sent daily. Phishing attacks are one the greatest forms of a cybersecurity attack, as we are quite easily trapped in them.

4.Keep track of your digital footprint
It’s vital to keep track of your digital footprint, including social media, and to remove accounts you’re not using. You should also ensure to set a strong password for your accounts.

5.Keep up with updates
Software companies sometimes may issue a security threat to their software. If you find these updates rather annoying then consider the situation if you are rather infected by those viruses. So follow the instruction or security alerts issued by a software company. When you update your system regularly, then you can avoid major security threats. Updates include vital security that helps to protect against known bugs and vulnerabilities. You should try to keep your software and devices up-to-date to avoid any intrusion.
6.Secure your mobile device
Securing your computer desktop isn’t the only thing. You also have to secure your mobile phone. Use a strong password and biometric features and ensure you have disabled your WIFI or Bluetooth, never connect to a public WIFI automatically and download things with precautionary measures.

7.Beware of social engineering
Don’t share WhatsApp numbers or contact numbers on social media openly. Beware of hackers may also contact you, this kind of attack may not be on your system but hackers find different ways to dupe you.
8.Back-up your data
These days storage doesn’t cost you a lot, so it’s not an excuse that you haven’t created a backup for your important data.
9.Use security software
Use security software, such as anti-spyware, anti-malware, and anti-virus programs. These security checks help to detect and remove malicious code if it slips into your network.
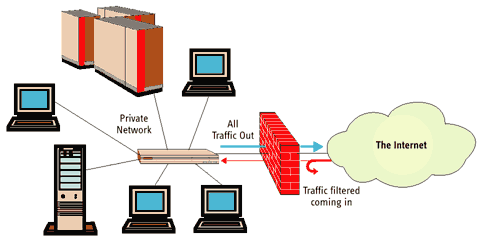
10.Put up a firewall
A firewall acts as a gatekeeper between your computer and the internet. A firewall is a major barrier to prevent cyber-attack such as viruses and malware. Try to update your firewall regularly and make sure that you have installed the latest version. Otherwise, they may not be fully effective.
You’re not immune
The most damaging thought you can have is “it won’t take place to me,” or “I don’t visit insecure websites.” Cybercriminals don’t distinguish in targeting all sorts of users. Be practical. Not all errors can be undone with “ctrl + Z”. Easy cyber safety tips like these can go a long way in averting a misfortune, but we have only scratched the surface of how your users can be knowledgeable and secure. Beware you are a target, never consider that you are safe from cyber attack.